Member-only story
Understanding Falco: Enhancing Kubernetes security through runtime monitoring
When utilizing Kubernetes as an orchestrator, securing our deployments and pods is of paramount importance. This is primarily due to multiple teams and developers deploying images whose construction details and associated permissions or privileges may not be fully known or understood.
However, there are numerous scanners available that can help detect violations. These can be seamlessly integrated with our monitoring and alerting tools to ensure ongoing security management of our deployment environment.

Falco
Falco is an open-source project, currently incubating under the Cloud Native Computing Foundation (CNCF). It operates as a runtime, leveraging kernel system calls to monitor and assert streams against a rule engine. If a rule violation is detected, Falco triggers an alert.
In our Kubernetes worker nodes, we have the option to run Falco either as a systemd service or directly from the command line.
Rules
- Predefined rules:
There is a predefined rules file located at “/etc/falco/falco_rules.yaml” that contains a set of rules designed to cover a variety of cases. However, it’s important to note that this file cannot be modified as it is replaced during a version upgrade. - Local rules:
The file “/etc/falco/falco_rules.local.yaml” is initially empty and is designed for you to override, modify, or add to the existing rule set.
Format output
There is many supported fields that we can use to format our output
https://falco.org/docs/rules/supported-fields/
Example
Go to “/etc/falco/falco_rules.yaml”
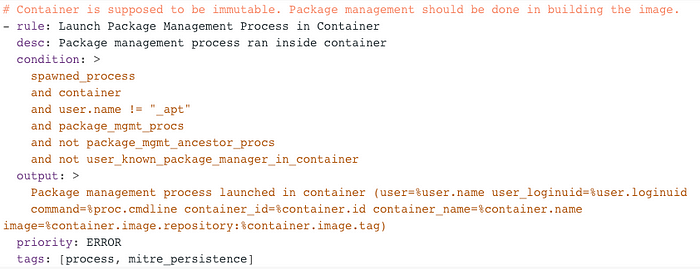
Copy and paste your rule into a local file located at “/etc/falco/falco_rules.yaml”. Subsequently, modify it to match the necessary format:
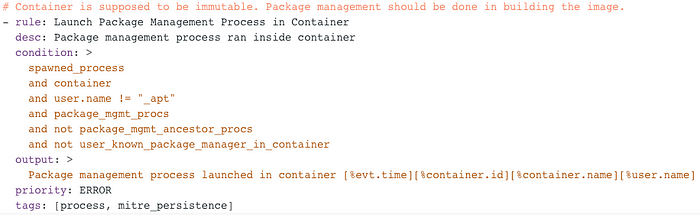
Finally, to receive formatted output, execute the following command to run Falco:
root@cluster:# falco | grep “Package management”
